Error message
Deprecated function: pathinfo(): Passing null to parameter #1 ($path) of type string is deprecated in Drupal\image\Entity\ImageStyle->supportsUri() (line 389 of core/modules/image/src/Entity/ImageStyle.php).
Shreeji Doshi is working with our cyber advisory team as its director of governance, risk and compliance, and he is an associate member of the Belgian Cyber Security Coalition. As part of the DORA Talks podcast series, Shreeji spoke to experts from around Thomas Murray about the impact of the EU’s Digital Operational Resilience Act (DORA).
This article is based on the transcription of Shreeji’s interview with Kevin Groves. Kev is a director of our Cyber Risk team. In the episode, Kev grilled Shreeji about what the EU regulators are hoping to achieve with DORA, and what affected entities can expect DORA to demand of them, both at a regulatory level and in terms of time, resources and software capabilities.


Kevin Groves
First of all, just keen to get your take on DORA in general, and give us a bit of background on why DORA and why now.
Shreeji Doshi
I think it's a great place to start. Well, the journey started in 2020 with the European Commission publishing a proposal as a part of wider digital finance package. And the need for it was quite evident. It was because cyber attacks were on the rise and they had ripple effects on everyone.
It's so nice to see a regulator taking notice of it and acting on it. In my personal opinion, it's a little bit too late, but at least it has happened. The objective is given away by the name of the Act quite nicely. It speaks about operational resilience, so “Digital Operational Resilience Act” – it’s quite an apt name: to ensure resiliency within the financial industry against the evolving digital and cyber threat landscape.

Kevin Groves
Who is affected by the new regulation?
Shreeji Doshi
This is one thing which I love about this specific regulation. Typically, the financial industry is known to be heavily regulated, but the supervisory action was centred on big banks, systematically important banks, insurance players, FMIs, they were heavily regulated by central, national banks.
Now what DORA is doing is widening this net to a host of other industry players in the financial service industries. It's no longer just banks or insurance. It goes to pension funds, it goes to investment funds, even crowd funding service providers. So it's broadening that scope, which I think was the need and they’ve acted well on that.

Kevin Groves
Just to outline the key kind of requirements that DORA has set up for these entities, can you go into that a little bit further?
Shreeji Doshi
Sure. But before we get into that, I think there is one aspect of the first two points that we discussed on the scope and the objectives. I think the requirements that are there in the regulation is one end of that, that what they want to do is harmonise how each of these organisations, irrespective of the size, manage risk in a consistent way.
So it’s prescriptive as to what organisations need to do from a risk management point of view. It's establishing frameworks, establishing governance, establishing requirements around protection, detection, identification, response and recovery. It's going to that level of detail – but it's harmonised, meaning that everyone would be adopting more or less similar practices, that is, governing the requirements that are there within the DORA regulation.
There are also small new ones that have already simplified the risk management framework for us, a very small subset of organisations. But barring that, everything needs to happen in a harmonised way across all of these type of organisations I spoke about. So it has provided mandatory requirements in four areas, which is around ICT risk management framework.
Then you have elements around incident management, so information and communication technology (ICT)-related incident management and reporting. Then you have digital operational resilience testing, which is more around technical testing and ICT third-party risk management (TPRM). There are mandated requirements. And then on a voluntary basis, there are also requirements around information sharing. And if you go one level deeper into each of these four pillars for now on the ICT-risk management, what the regulator is pushing is that all these organisations need to establish some sort of governance where a management body has to be delegated the authority of managing ICT risk, along with setting up a risk management framework that is quite holistic, covers all areas of cyber security, all information security, all ICT risk.
And there has to be some element of learning, evolving continuous improvements around this, which is great. On the incident management reporting, we will have a separate session on that, but it's providing requirements on what are the various ways your organisation needs to classify an ICT incident and what are the thresholds of reporting a major incident.
So it's fairly prescriptive in that way on digital operational resilience testing. It is mandating organisations to perform technical tests, like threat-led penetration testing, which was to an extent implemented to work within the banking sector. But now the scope is far broader. Then, on the ICT TPRM framework, there are so many prescriptive requirements coming around what kind of standard contractual process you have, what kind of risk do you assess from a third-party point of view or concentration-related risk?
It's quite holistic. It's so good to see a regulatory approach where there are such prescriptive requirements around all of these topics.

Compliance Digest Newsletter
Subscribe to DORA Digest and stay up to date with the key issues
and developments unfolding as the countdown to DORA begins.
Kevin Groves
And I suppose the timescales on this are approaching pretty fast, less than a year now until January ‘25 for implementation. Any ideas on the types of enforcement that'll be brought in post-17 January ‘25?
Shreeji Doshi
The regulation offers supervisory mechanisms to be enforced which could be financial in nature, such as administrative fines. There could be public reprimands, there could be a push on solving certain issues or gaps identified by the regulator. It could also be compensation for any losses borne by customers which can directly be attributed to non-compliance.
So, there is an element of multiple levers that the regulation has offered to the competent authorities from a supervisory mechanism point of view.
Kevin Groves
Understood. And you mentioned there a gap assessment. Can you just outline, you know, our approach to running a gap assessment on behalf of organisations?
Shreeji Doshi
Yeah, I think every organisation, if they want to do a compliance journey gap assessment, that would be the first step as it's a no-brainer.
Basically, it's looking at the regulation and turning it into a questionnaire. Using this questionnaire, organisations can perform a self-assessment of sorts, and then benchmark themselves on how far they are from compliance. Or there could be organisations that could take services where there is some element of support around conducting interviews, identifying gaps, documenting and providing a complete compliance journey.
This approach would be more useful, because you would get an external view and I think it would provide assurance to the wider business that the organisation's taking the right steps from a compliance point of view. So there could be multiple ways in which organisations could go about doing this gap assessment.
Kevin Groves
Right. And I guess Thomas Murray's gap assessments, the outputs and deliverables from that would be, ultimately, a compliance roadmap.
What would be the key ways that Thomas Murray might support an organisation with that ongoing compliance piece?
Shreeji Doshi
Where Thomas Murray would be able to support is on multiple aspects, I think all the requirements that are there within DORA. We have internal competency at the technology level. If you want to perform a risk assessment or conduct assessments of third parties, we have a technology platform that supports it.
We have internal competency of performing incident response and have experienced people who have been in incident response for a long time, and they can help organisations improve their processes or help organisations respond to an incident that they're facing.
On the testing side, we have competency to do those tests that are required by the regulation. Generally, we offer consulting services to help organisations on the compliance journey.
So we can offer senior people advice on each of these requirements initially.
Kevin Groves
Excellent. So really helping with readiness, overseeing and managing the overall approach, and then obviously supporting those organisations to enhance and optimise any of their control frameworks and so on.

Kevin Groves
How will most entities affected by DORA be taking this from an investment perspective?
How much time, effort, resource software capability is going to be required?
Shreeji Doshi
There are certain, quite mature organisations on the security majority scale, and they have already done a DORA gap assessment. They have a full nine month-programme from a compliance point of view. So if a mature organisation is undertaking steps to have a compliance journey which lasts nine months, I think it's safe to say most organisations would need to find investment.
There are so many requirements in DORA that may require redoing the processes that you already have, which means that you need to train people, you need to factor in an element of change management. So investment in time, resources, all of that needs to be factored in, along with the various BAU work that creates the usual challenges.
And there are certain requirements that might even warrant getting additional software capabilities. You know, if you have to manage third parties in a consistent way, if you have to record risk and report it, you may want to have to not do that on an Excel sheet or with an ad hoc solution.
So it would kind of require organisations to invest on multiple fronts that will stem from a gap assessment, that would be the cornerstone of everything.
Kevin Groves
That was going to be my next question, actually. I think running that initial gap assessment is where you’re ultimately going to pull out the future requirements and have a much clearer and better understanding. Brilliant. Well, thank you Shreeji.
Shreeji Doshi
Super. Thanks, Kev.
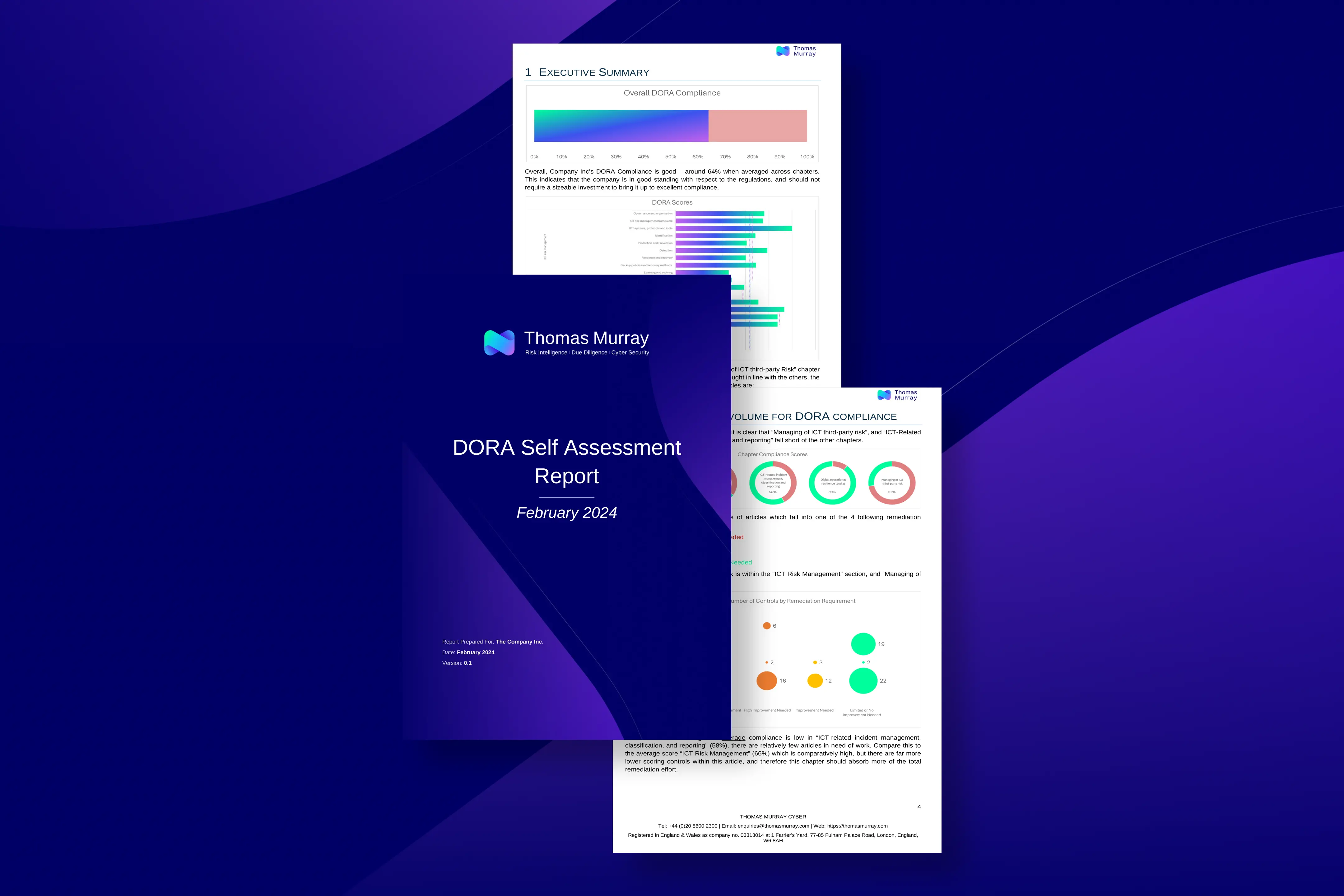
Are you ready for DORA?
Use our free, easy-to-follow Readiness Toolkit to determine how close your organisation is to meeting all the Digital Operational Resilience Act (DORA) requirements. Once completed, we’ll send you a free report outlining how prepared you are for DORA. You can use our output to create an action plan to achieve compliance by 17 January 2025.
Insights

Thomas Murray Risk Update: Middle East Developments – Impact on Post-Trade and Capital Markets
Thomas Murray’s Risk Committee (RC) met today to assess the rapidly evolving geopolitical situation in the Middle East.

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.


